Abstract
In recent years, we have witnessed that technology has advanced dramatically. While new, hi-tech, automated devices entered our lives, a tendency of moving from the disjointed nature of objects to a more interconnected world has emerged. Although such need of interconnection was originated in the IT industry and with the Internet of Things (IoT), automotive industry was also affected by such a trend. Connected, electric, highly-automated and autonomous vehicles are making their way into our lives. As a result of this paradigm shift, new security challenges are introduced in the automotive industry. Vehicles are comprised of tens or sometimes a hundred of computers, also known as Electronic Control Units (ECUs) that need to communicate and be interconnected in order for the vehicle to function properly. Protecting vehicles from potential threats and attacks that may compromise the security and consequently the safety of both the vehicle and the passenger is of great importance. Hence, a comprehensible attack analysis methodology is needed to model the possible attacks in vehicles. Attack analysis is part of the risk assessment process. To have an accurate risk analysis, two factors are needed: first, the impact of an attack vector, which is not the subject of this thesis, and second, the feasibility of an attack path which is what we address as a part of our thesis using the nominated attack analysis methodology. In this thesis, we investigate existing methodologies for modelling attacks and try to nominate one that is most suitable for the automotive industry. This judgement is based on a list of criteria that are collected either through surveying previous related works or through interviewing industrial and academic experts. Once the methodology is nominated, we introduce a method for calculating the feasibility of different possible attack paths using the proposed methodology. Finally, we use some use cases by means of which we demonstrate how our nominated method can be used to model attacks against some assets and how the feasibility of each attack vector can be calculated for the use cases.
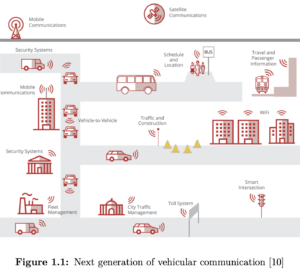
1.1 Background The current automotive industry is leading toward producing vehicles with autonomous driving or an advanced driver-assistance system [4]. In order to fulfill such smart capabilities and also equip the vehicle with more functional features such as Intelligent Transport Systems (ITS), different levels of connectivity needs to be considered in the architecture level. Different communication channels are being developed such as vehicle-to-vehicle (V2V) and vehicle-to-infrastructure (V2I) in order to fulfill ITS different goals, including increase of roads safety and traffic flow [5]. Moreover, vehicles also need to become connected to the Cloud services for remote diagnostics or remote software updates [6], [7]. Figure 1.1 illustrates this connection and communication. Although the evolution trend seems to bring more functionality and intelligence into the automotive sector, however, this can also make modern vehicles subject to various types of intrusion and malicious activities which could be considered as major threats to both the humans factor and the vehicle itself. In order to provide inter-connectivity, connected vehicles rely on wireless and cellular communication interfaces. This exposes them to a wide range of security risks. In 2015, Miller and Valasek [8] performed a research on possible remote attacks on vehicles and they succeeded in breaking into a Jeep Cherokee and consequently taking control over the steering and the braking systems. In the big rig truck’s scenario which happened in 2016, attackers succeeded to gain control over the accelerator and the braking system [9]. Lack of safety in a vehicle could lead to major disasters such as loss of life, therefore security breaches are highly intolerable in automotive industry. As a result, there is an ever-increasing public concern toward the cybersecurity of autonomous and connected vehicles [10].
In order to tackle cybersecurity concerns in the automotive industry, threat modeling and risk assessment frameworks have been developed [11]. Risk assessment methods usually start with the asset identification step where critical assets are identified. Then by considering standard damage scenarios, different threats to those assets are classified via threat analysis procedures. Thereafter, impact assessment is done by determining the impact levels associated with a compromised asset. As the security design process proceeds, different vulnerabilities may emerge through the vulnerability analysis stage. Eventually, by means of a comprehensive attack analysis method, potential attack paths and their associated feasibility are analyzed. The results derived from the risk assessment process are the basis upon which the risk treatment is applied as the closing stage [12].
